



A group of NATO Cooperative Cyber Defence Centre of Excellence (CCD COE) researchers have concluded that the global outbreak of NotPetya malware on June 27 could likely be attributed to a 'state actor'.
In a press release on June 30, Bernhards Blumbergs of NATO CCD COE said, "In the case of NotPetya, significant improvements have been made to create a new breed of ultimate threat."
NATO’s Secretary General reaffirmed on June 28 that a cyber operation with consequences comparable to an armed attack can trigger Article 5 of the North Atlantic Treaty and trigger responses responses through military means, the release said.
“If the operation could be linked to an ongoing international armed conflict, then law of armed conflict would apply, at least to the extent that injury or physical damage was caused by it, and with respect to possible direct participation in hostilities by civilian hackers, but so far there are reports of neither,” said Tomáš Minárik, researcher at NATO CCD COE Law Branch.
Minárik further said that this can give the targeted states options to respond with countermeasures.
"A countermeasure could be, for example, a cyber operation sabotaging the offending state’s government IT systems, but it does not necessarily have to be conducted by cyber means. In any case, the effects of a countermeasure must not amount to a use of force or affect third countries," he said.
NotPetya comes at a very unfortunate time.
The global community already has its hands tied with geopolitical tensions in the middle-east, and the conflict between US and North Korea. If that was not enough, the alleged hacking efforts made by Russia in the 2016 US Presidential Elections has kept bilateral ties tense between the US intelligence community and the Kremlin.
The assumption made by NATO CCD COE researchers of a 'state actor' being behind the cyber attack seems more plausible now as many cyber security firms have concluded that NotPetya was meant for destructive purposes rather that financial gains.
Followed by Kaspersky Lab and Comae Technologies, security firms Cisco Talos, F-Secure, and Malwarebytes are also now supporting the theory of NotPetya being a wiper disguised as a ransomware which was designed to cause chaos.
The scale and nature of this attack is so large that cybersecurity experts dub it as 'WannCry, but done by pros' and say that 'NotPetya is the most hazardous ransomwares in cyber history'.
After an analyses, cybersecurity firm Kaspersky concluded that NotPetya was not designed for financial gains.
“What does it mean? Well, first of all, this is the worst-case news for the victims – even if they pay the ransom they will not get their data back. Secondly, this reinforces the theory that the main goal of the ExPetr attack was not financially motivated, but destructive,” Kaspersky said in their blog.
"Given the circumstances of this attack, Talos assesses with high confidence that the intent of the actor behind Nyetya was destructive in nature and not economically motivated," Cisco Talos said.
NATO also said that cyber criminals are not behind this as the method for collecting the ransom is poorly designed and the ransom would probably not even cover the cost of the operation.
The attackers have demanded USD 300 in Bitcoin in exchange for the decryption key, and have left the email ID: wowsmith123456@posteo.net as part of the contact details.
Apparently, the attackers have had their email address blocked by the provider due to which not much money has been sent as ransom.
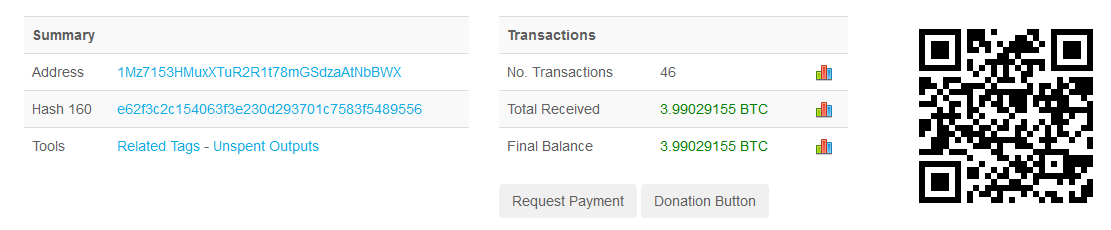
As shown in the image above, the hackers got only around 4 bitcoins (~USD 10,000) as ransom money.
"According to our current knowledge, the malware is intentionally corrupt in a way that the Salsa key was never meant to be restored. Nevertheless, it is still effective in making people pay ransom. [...] If you are a victim of this malware and you are thinking about paying the ransom, we warn you: Don’t do this. It is a scam and you will most probably never get your data back," Malwarebytes said.
What NotPetya did?“Unlike WannaCry, Petya encrypts MFT (Master File Tree) tables for NTFS partitions and overwrites the MBR (Master Boot Record) with a custom bootloader that limits the access of its victims only to the ransom note and prevents the infected computers from booting. Due to this, Petya can be considered more dangerous and intrusive compared to WannaCry or any other strains of ransomware,” says Souti Dutta, Lead Threat Analyst, SOC Services at Paladion.
“NotPetya malware is behind what is quickly emerging as another devastating global ransomware incident, one with the potential to be even more damaging than WannaCry,” says Kobi Ben Naim, Senior Director of Cyber Research, CyberArk Labs.
“Initially thought to be a strain of the powerful Petya ransomware, NotPetya is spreading using the incredibly efficient infection method used by WannaCry - a worm that quickly spreads the ransomware using the “eternalblue” SMB vulnerability in Microsoft systems. The combination is potent and has the potential to inflict massive damage on scales we have not witnessed before,” Naim adds.
Most ransomware infections target and encrypt files on the hard disk but the victim can still use the operating system (OS), whereas, Petya takes it a step further as it locks portions of the hard drive itself which makes it impossible to access anything on the drive, including the Windows OS.
While many now term NotPetya as wiper but strictly speaking it is not one. Instead of wiping the data, what it has done is simply locked the PCs of its victims and thrown away the keys.
Whether state sponsored or not, such cyberattacks cost organisations a lot of money. By 2021, cyber crime damages are expected to cost the world around USD 6 trillion annually. If it leads to a war, then these costs can jump exponentially.

Discover the latest Business News, Sensex, and Nifty updates. Obtain Personal Finance insights, tax queries, and expert opinions on Moneycontrol or download the Moneycontrol App to stay updated!
Find the best of Al News in one place, specially curated for you every weekend.
Stay on top of the latest tech trends and biggest startup news.